SMS Spoofing, a sophisticated form of cyber attack, has emerged as a significant concern in today’s interconnected world. Understanding its nature and implications is crucial for individuals and organizations alike.
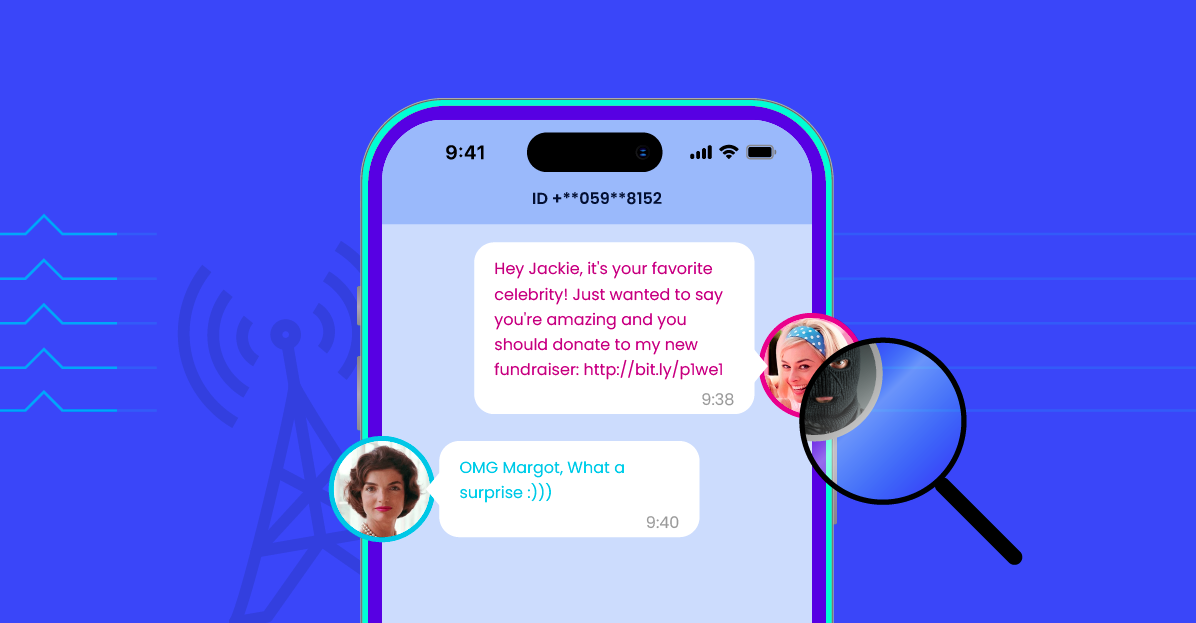
Understanding How SMS Spoofing Works
SMS spoofing is a technique used by individuals with malicious intent to manipulate the sender information displayed on a recipient’s mobile device when they receive a text message. Here’s how it works:
- Sender Information Manipulation: SMS spoofing involves the manipulation of the sender information that accompanies an SMS message. This includes the sender’s phone number or name that appears on the recipient’s device.
- Sender Identification: When a regular SMS message is sent, the sender’s phone number or name is typically displayed on the recipient’s device. This information helps the recipient identify who sent the message.
- Spoofing Tools: To spoof an SMS message, individuals use specialized software or online services that allow them to manipulate the sender’s information. These tools enable the sender to input any desired sender information, including phone numbers and names.
- Gateway Manipulation: SMS spoofing often involves utilizing SMS gateways, which are intermediaries that transmit SMS messages between different networks. By exploiting vulnerabilities or weaknesses in these gateways, spoofers can inject false sender information into the messages they send.
- Masking Original Sender: The goal of SMS spoofing is to mask the original sender’s identity and impersonate someone else. This can be done for various reasons, such as phishing attempts, fraudulent activities, or pranks.
- Legitimate Uses: While SMS spoofing is often associated with malicious activities, there are also legitimate uses for it. For example, businesses may use SMS spoofing services to send messages with a consistent sender ID to their customers, such as using their brand name instead of a phone number.
- Security Concerns: SMS spoofing poses significant security concerns, as it can be used for various types of fraud, including phishing scams, identity theft, and social engineering attacks. It can also undermine the trustworthiness of SMS messages, as recipients may be unable to verify the true identity of the sender.
- Regulatory Measures: To combat SMS spoofing and protect consumers, regulatory authorities and mobile network operators have implemented measures such as sender authentication protocols and blocking suspicious messages. However, spoofers continue to adapt their techniques to evade detection and enforcement efforts.
In summary, SMS spoofing is a deceptive practice that involves manipulating sender information to disguise the true origin of a text message. While it can have legitimate uses, it is often exploited for malicious purposes, highlighting the importance of vigilance and security measures to mitigate the risks associated with this technique.
Implications of SMS Spoofing
SMS spoofing can have significant implications across various aspects of communication and security:
- Identity Theft: One of the most serious implications of SMS spoofing is the potential for identity theft. By impersonating someone else through spoofed SMS messages, attackers can trick individuals into providing sensitive information such as passwords, account numbers, or personal details.
- Financial Fraud: SMS spoofing can be used as a tool for financial fraud. Attackers may send spoofed messages pretending to be from banks, financial institutions, or payment services, requesting account information or initiating unauthorized transactions.
- Phishing Attacks: SMS spoofing is commonly used in phishing attacks, where attackers impersonate trusted entities to deceive recipients into clicking on malicious links, downloading malware-infected files, or disclosing confidential information.
- Social Engineering: SMS spoofing enables social engineering attacks by manipulating the sender’s information to gain the trust of recipients. Attackers can use spoofed messages to trick individuals into revealing sensitive information or performing actions that compromise security.
- Reputation Damage: Organizations and individuals may suffer reputational damage if their identities are spoofed to perpetrate fraudulent activities or distribute malicious content. Victims of spoofing attacks may lose trust in the legitimacy of communications from the spoofed entity.
- Legal and Compliance Risks: SMS spoofing may violate laws and regulations related to telecommunications, consumer protection, and data privacy. Organizations found to be involved in SMS spoofing activities may face legal consequences, regulatory fines, and damage to their reputation.
- Impact on Communication Infrastructure: SMS spoofing can undermine the reliability and integrity of communication infrastructure by allowing malicious actors to exploit vulnerabilities in SMS gateways and protocols. This can result in disruptions to communication networks and services.
- Loss of Confidentiality: SMS spoofing can compromise the confidentiality of sensitive information transmitted via text messages. If attackers gain unauthorized access to spoofed messages, they may intercept sensitive data, such as authentication codes or confidential communications.
- Misinformation and Disinformation: SMS spoofing can be used to spread misinformation, disinformation, and malicious content. Attackers may impersonate legitimate sources to disseminate false information, manipulate public opinion, or incite panic and confusion.
Common Targets of SMS Spoofing
SMS spoofing can target a wide range of individuals, organizations, and entities. Some common targets of SMS spoofing include:
- Individuals: Every day individuals are often targeted by SMS spoofing attacks, especially those who may not be aware of the risks associated with fraudulent messages. Attackers may attempt to trick individuals into providing personal information, such as login credentials, financial details, or social security numbers.
- Financial Institutions: Banks, credit unions, and other financial institutions are prime targets for SMS spoofing attacks. Attackers may impersonate these institutions to send fraudulent messages requesting account information, PINs, or verification codes to facilitate unauthorized transactions or identity theft.
- E-commerce Platforms: Online retailers and e-commerce platforms may be targeted by SMS spoofing attacks aimed at stealing customer account credentials, payment information, or sensitive transaction data. Attackers may impersonate these platforms to lure users into clicking on malicious links or providing confidential information.
- Government Agencies: Government agencies, including tax authorities, immigration services, and law enforcement agencies, may be targeted by SMS spoofing attacks designed to deceive individuals into disclosing personal information, responding to fake emergencies, or complying with fraudulent requests.
- Healthcare Providers: Healthcare organizations, medical facilities, and insurance companies are potential targets for SMS spoofing attacks seeking to obtain sensitive patient information, medical records, or insurance details. Attackers may exploit vulnerabilities in communication channels to impersonate healthcare providers or insurers.
- Corporate Enterprises: Large corporations, small businesses, and enterprises across various industries may be targeted by SMS spoofing attacks aimed at compromising employee accounts, stealing proprietary information, or conducting corporate espionage. Attackers may use spoofed messages to impersonate executives, employees, or business partners.
- Social Media Platforms: Social media platforms and messaging apps are common targets for SMS spoofing attacks seeking to compromise user accounts, distribute malware, or spread phishing scams. Attackers may send spoofed messages pretending to be from social media platforms to trick users into clicking on malicious links or disclosing account credentials.
- Mobile Network Operators: Mobile network operators and telecommunications companies themselves may be targeted by SMS spoofing attacks aimed at exploiting vulnerabilities in their infrastructure, compromising subscriber accounts, or disrupting communication services. Attackers may impersonate network operators to deceive customers or gain unauthorized access to network resources.
How SMS Spoofing Can Be Exploited
SMS spoofing can be exploited in various ways, primarily due to its ability to deceive recipients into believing that a message is from a trusted source when it’s not. Here are some ways SMS spoofing can be exploited:
- Phishing Attacks: Attackers can send spoofed SMS messages posing as legitimate institutions such as banks, government agencies, or service providers. These messages often contain links or instructions prompting recipients to provide sensitive information like passwords, credit card numbers, or personal details.
- Identity Theft: By impersonating someone else via spoofed SMS messages, attackers can trick individuals into revealing personal information, and login credentials, or even authorizing transactions on their behalf. This can lead to identity theft and financial loss.
- Malware Distribution: SMS spoofing can be used to distribute malware by sending messages containing malicious links or attachments. Unsuspecting recipients may click on these links or download attachments, unknowingly compromising the security of their devices.
- Social Engineering Attacks: Attackers can exploit SMS spoofing to conduct social engineering attacks, such as impersonating a friend or family member to gain trust and manipulate recipients into disclosing sensitive information or performing certain actions.
- Fraudulent Transactions: By spoofing SMS messages from financial institutions or payment processors, attackers can trick individuals into authorizing fraudulent transactions or providing one-time passwords (OTPs) used for two-factor authentication (2FA), thereby gaining unauthorized access to accounts.
- Disruption of Communication: In some cases, SMS spoofing can be used to disrupt communication by flooding recipients with a large volume of spoofed messages, causing confusion or making it difficult to distinguish legitimate messages from fraudulent ones.
Legal and Ethical Considerations
SMS spoofing, the practice of disguising the origin of a text message by manipulating the sender’s information, raises significant legal and ethical concerns. Below are some key considerations:
Legal Considerations:
- Violation of Laws: SMS spoofing may violate various laws, including:
- Telecommunications Act: Many countries have laws governing telecommunications that prohibit the unauthorized manipulation of caller ID information.
- Fraud and Deception Laws: SMS spoofing with malicious intent can constitute fraud or deception, which is illegal in most jurisdictions.
- Privacy Laws: Infringing upon individuals’ privacy rights by impersonating someone else through SMS spoofing can lead to legal repercussions.
- Federal Communication Commission (FCC) Regulations: In the United States, the FCC has regulations specifically addressing caller ID spoofing and its prohibition, particularly when it involves telemarketing or other malicious activities.
- Consent Requirements: Depending on the jurisdiction, obtaining consent from all parties involved before spoofing SMS messages may be necessary to comply with legal standards.
- Criminal Offenses: Engaging in SMS spoofing for illegal purposes, such as harassment, extortion, or phishing, can result in criminal charges.
- Civil Liability: Victims of SMS spoofing may pursue civil lawsuits against perpetrators for damages incurred, including financial losses or emotional distress.
Ethical Considerations:
- Privacy Violation: SMS spoofing violates individuals’ privacy by impersonating them or misleading recipients about the true identity of the sender.
- Trust and Integrity: SMS spoofing undermines trust in communication networks and erodes the integrity of messaging systems by allowing for deceptive practices.
- Potential for Harm: Spoofed messages can cause harm to individuals or organizations, leading to reputational damage, financial losses, or emotional distress.
- Fairness and Honesty: Engaging in SMS spoofing contradicts principles of fairness and honesty in interpersonal communication and business interactions.
- Impact on Society: Widespread misuse of SMS spoofing technology can have broader societal implications, including increased skepticism and decreased trust in digital communications.
In summary, SMS spoofing presents significant legal and ethical challenges due to its potential for misuse and harm. Individuals and organizations need to understand and adhere to relevant laws and ethical standards to mitigate the risks associated with this practice.
Ways to Detect SMS Spoofing
Detecting SMS spoofing can be challenging, but there are a few methods you can use to increase your chances of detecting it:
- Check Sender ID: Pay attention to the sender’s phone number or alphanumeric sender ID. If the sender ID looks suspicious or unfamiliar, it could be a sign of spoofing.
- Verify Message Content: Be cautious of messages that ask for sensitive information or request urgent actions, especially if they’re unexpected. Legitimate organizations usually don’t ask for personal or financial information via SMS.
- Confirm with Sender: If you receive a suspicious message from someone you know, consider contacting the sender through a different channel (e.g., phone call or email) to verify the authenticity of the message.
- Analyze Message Headers: Advanced users can inspect the message headers to look for inconsistencies or signs of manipulation. This method requires technical expertise and access to messaging platforms that allow header inspection.
- Use Anti-Spoofing Solutions: Some telecom providers and messaging platforms offer anti-spoofing solutions that analyze incoming messages for signs of spoofing. Consider using these services to enhance your protection against spoofed messages.
- Educate Users: Educate yourself and others about the risks of SMS spoofing and the common tactics used by attackers. Awareness can help individuals recognize and respond to suspicious messages effectively.
- Report Suspicious Messages: If you suspect SMS spoofing, report the message to your telecom provider or relevant authorities. Reporting suspicious activities can help prevent future incidents and protect other users.
While these methods can help detect SMS spoofing, it’s important to remember that no detection method is foolproof. Stay vigilant and exercise caution when interacting with SMS messages, especially those from unknown or untrusted sources.
Preventive Measures Against SMS Spoofing
Implementing robust security measures, such as two-factor authentication and encryption, can bolster defenses against SMS Spoofing attacks. Proactive measures are critical in safeguarding sensitive information.
Best Practices for SMS Security
Educating users about SMS security risks and promoting vigilance can significantly reduce the likelihood of falling victim to SMS Spoofing attacks. Regular updates and patches help maintain system integrity.
Role of Service Providers in Preventing SMS Spoofing
Service providers play a pivotal role in combating SMS Spoofing by adhering to industry standards and collaborating with law enforcement agencies. Collective efforts are essential for effective mitigation strategies.
Case Studies: Successful Mitigation of SMS Spoofing Attacks
Examining real-world examples sheds light on effective strategies for mitigating SMS Spoofing attacks across various sectors, including banking and telecommunications.
Challenges in Combating SMS Spoofing
Technological limitations and the evolving tactics of attackers pose significant challenges in combating SMS Spoofing. Continuous innovation and adaptation are necessary to stay ahead of emerging threats.
Emerging Technologies to Counter SMS Spoofing
Advancements in AI and blockchain technology offer promising avenues for detecting and preventing SMS Spoofing attacks. Integration of these technologies enhances security posture and resilience.
Global Efforts to Address SMS Spoofing
International cooperation and awareness campaigns play crucial roles in addressing the global threat landscape posed by SMS Spoofing. Collaboration among stakeholders fosters a united front against cyber threats.
Recent Developments and Trends
The landscape of SMS spoofing continues to evolve, with attackers employing increasingly sophisticated techniques. Regulatory responses and technological innovations shape the trajectory of SMS security.
Regulators and technology providers are constantly adapting to address the challenges posed by SMS spoofing. Regulatory bodies may enact laws and guidelines to hold telecommunication companies accountable for safeguarding their networks against spoofing attacks. These regulations may require telecom companies to implement stronger authentication mechanisms and monitoring systems to detect and prevent fraudulent SMS activities.
Moreover, technological innovations play a crucial role in enhancing SMS security. Telecom companies and security firms develop advanced algorithms and protocols to authenticate the origin of SMS messages and verify the identity of senders. Implementing technologies such as digital signatures and cryptographic protocols can help mitigate the risks associated with SMS spoofing.
Additionally, network operators may deploy machine learning algorithms and artificial intelligence systems to analyze patterns and detect anomalies in SMS traffic. These systems can identify suspicious behavior, such as mass SMS campaigns originating from unauthorized sources, and take proactive measures to block or quarantine malicious messages.
Furthermore, end-users play a vital role in mitigating the impact of SMS spoofing by exercising caution and adopting best practices. Individuals should be vigilant of suspicious SMS messages, especially those requesting sensitive information or containing unusual links or attachments. By educating users about the risks of SMS spoofing and promoting cybersecurity awareness, organizations can empower individuals to recognize and report potential threats effectively.
The Future of SMS Security
The future of SMS (Short Message Service) security is expected to evolve in response to emerging threats and advancements in technology. Here are some key trends and potential developments that could shape the future of SMS security:
- End-to-end Encryption: As privacy concerns grow, there will likely be increased demand for end-to-end encryption in SMS messaging. This means that only the sender and the recipient will have access to the content of the messages, making it more difficult for hackers and third parties to intercept or read the messages.
- Multi-Factor Authentication (MFA): SMS is commonly used as a second factor in multi-factor authentication systems. However, SMS-based MFA is not foolproof, as SIM swapping attacks and SMS interception techniques have been exploited by attackers. In the future, there may be a shift towards more secure methods of authentication, such as biometrics or hardware tokens, reducing reliance on SMS for MFA.
- Blockchain-based Solutions: Blockchain technology has the potential to enhance SMS security by providing a decentralized and tamper-resistant infrastructure for message transmission and verification. Blockchain-based SMS platforms could offer improved authentication and verification mechanisms, as well as enhanced privacy and integrity of messages.
- AI-Powered Threat Detection: With the help of artificial intelligence and machine learning algorithms, SMS security solutions can become more proactive in detecting and preventing security threats. AI-powered systems can analyze patterns of SMS usage, detect suspicious activities, and flag potential security breaches in real-time.
- Zero-Trust Frameworks: Zero-trust security frameworks advocate for the principle of “never trust, always verify.” In the context of SMS security, this means implementing strict access controls, continuous authentication, and encryption protocols to ensure the integrity and confidentiality of SMS communications.
- Regulatory Compliance: Governments and regulatory bodies may introduce stricter regulations and standards for SMS security, especially in industries dealing with sensitive information such as healthcare, finance, and government services. Compliance with regulations such as GDPR (General Data Protection Regulation) and HIPAA (Health Insurance Portability and Accountability Act) will drive the adoption of more secure SMS solutions.
- Biometric Authentication: Integration of biometric authentication methods, such as fingerprint scanning or facial recognition, could add an extra layer of security to SMS-based services, ensuring that only authorized users can access sensitive information transmitted via SMS.
Overall, the future of SMS security will be characterized by a combination of technological innovations, regulatory measures, and user awareness efforts aimed at addressing evolving threats and enhancing the confidentiality, integrity, and availability of SMS communications.
Conclusion
In conclusion, the pervasive threat of SMS Spoofing looms large over individuals and organizations globally, posing significant risks that demand urgent attention and proactive measures. As we delve deeper into the intricacies of this deceptive technique, it becomes evident that its ramifications extend far beyond mere inconvenience, potentially wreaking havoc on personal privacy, financial security, and the integrity of organizational operations.
The practice of SMS Spoofing, whereby malicious actors manipulate the originating address of text messages to deceive recipients, represents a formidable challenge in today’s interconnected digital landscape. With the ability to mimic legitimate entities and institutions, spoofed messages can lure unsuspecting users into divulging sensitive information, falling victim to phishing scams, or unwittingly facilitating unauthorized access to confidential systems.
Moreover, the proliferation of SMS Spoofing threatens to erode trust in communication channels essential for business transactions, customer interactions, and emergency notifications. The ease with which attackers can exploit vulnerabilities in telecommunications infrastructure underscores the pressing need for concerted efforts to fortify defenses and mitigate the inherent risks associated with this insidious threat.
Fortunately, by embracing a multi-faceted approach to cybersecurity, individuals and organizations can enhance their resilience against SMS Spoofing attacks and safeguard digital assets against exploitation. This entails cultivating a heightened awareness of common spoofing tactics, educating users about the telltale signs of fraudulent messages, and fostering a culture of vigilance in scrutinizing incoming communications for authenticity.
Furthermore, the adoption of robust security measures, such as implementing stringent authentication protocols, deploying intrusion detection systems, and leveraging advanced encryption technologies, can serve as formidable deterrents to would-be perpetrators seeking to exploit vulnerabilities in the SMS ecosystem.
Additionally, collaboration among telecommunications providers, regulatory agencies, and cybersecurity experts is imperative in developing comprehensive frameworks for detecting, mitigating, and responding to SMS Spoofing incidents on a global scale. By sharing threat intelligence, coordinating response efforts, and fostering a collective commitment to combating cyber threats, stakeholders can effectively stem the tide of spoofed messages and safeguard the integrity of communication networks.
In essence, while the specter of SMS Spoofing may loom ominously on the horizon, it is not an insurmountable challenge. Through proactive measures, diligent vigilance, and collaborative action, we can fortify our defenses, mitigate the risks posed by SMS Spoofing, and uphold the trust and security upon which our digital interactions depend. Together, we can turn the tide against cyber adversaries and pave the way for a safer, more resilient digital future.
